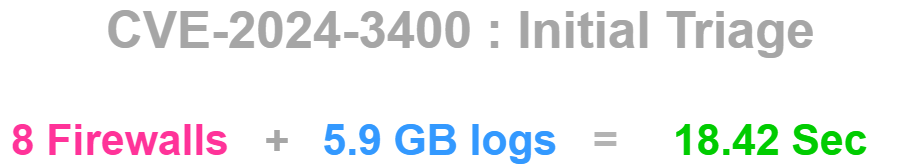Part 4.5 - Hunt for exploitation attempts by analyzing log files.
When responding to a security breach, one of the key objectives for the incident responder is to figure out the entry point or the Patient Zero. This can be quite challenging, as the customer may have more than one entry point to the infrastructure other than phishing the end user. We can make use of YARA rules when responding to similar breaches by targeting the compromised server or endpoint logs.
Detect CVE-2024-3400 exploitation in Palo Alto Networks PAN-OS
This was a quite recent exploitation and significantly affected many enterprises since a lot of them use Palo Alto firewalls. Since these appliances are hardened and completely locked down, it is extremely difficult to get disk image, especially when it is a physical appliance. The data dump extracted with the help of Palo Alto technical support was the first set of evidence for analysis when responding to this incident. The objective is to quickly look at the dump and see any signs of compromise. If yes, then kickstart the incident response and forensics.
I personally use Velociraptor for evidence triage; this is my personal choice (I have covered the capabilities of Velociraptor and YARA in much detail in the Ecosystem section.), and you can use any tool you are comfortable with. The tech-dump evidence I received for analysis was uploaded to my Velociraptor server in an FTP folder. I then ran YARA for quick triage, as shown below.
Believe me, it took less than 19 seconds to triage the firewall logs and determine which firewalls required further investigation.
You can leverage YARA rules for similar investigations when you have log files from a compromised device, server, or endpoint. The technical blog post will provide you with enough artifacts to write your own YARA rules if ready-made rules are not available.