Part 4.1 - Hunting for files with Stolen code-signing Cert.
In software, one way to establish trust in a code is by signing it with a trusted code signing certificate. This practice involves cryptographically signing software to increase trust and confidence. The operating system verifies these signatures through the concept of a certificate chain.
Threat actors often use this technique to bypass security controls when infecting an endpoint. Since the binary is signed by a third-party trusted authority, Windows operating systems tend to consider it legitimate software. In recent years, we have witnessed high-profile breaches where malware binaries were signed by trusted authorities.
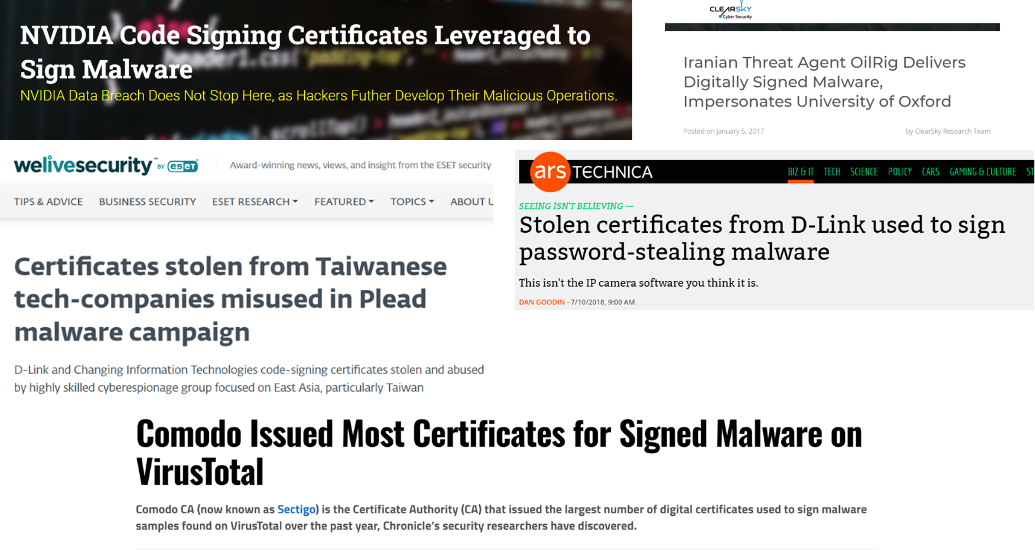
Here are some headlines related to threat actors exploiting trust by signing code with stolen certificates.
Authenticodeis a Microsoft code-signing technology that identifies the publisher of Authenticode-signed software and verifies that the software has not been tampered.
Here are some well-known certificates used for signing malware code. Refer to the project lolcerts to find more information on such certificates.
| Issuer | Serial | Status | Source |
| DigiCert [MicroStar(MSI)] | 0b:88:60:32:86:1d:95:53:c6:8f:80:33:13:a9:89:75 | revoked | leaked |
| VeriSign [NVIDIA] | 43:bb:43:7d:60:98:66:28:6d:d8:39:e1:d0:03:09:f5 | revoked | leaked |
| VeriSign [NVIDIA] | 14:78:1b:c8:62:e8:dc:50:3a:55:93:46:f5:dc:c5:18 | revoked | leaked |
| Sectigo [Hangil IT Co] | 01:39:dd:e1:19:bb:32:0d:fb:9f:5d:ef:e3:f7:12:45 | revoked | |
| DigiCert [AnyDesk] | 0d:bf:15:2d:ea:f0:b9:81:a8:a9:38:d5:3f:76:9d:b8 | revoked | leaked |
| VeriSign [HackingTeam] | 0f:1b:43:48:4a:13:69:c8:30:38:dc:24:e7:77:8b:7d | expired | malicious |
| LAMERA [dprk] | 87:9f:a9:42:f9:f0:97:b7:4f:d6:f7:da:bc:f1:74:5a | revoked | malicious |
To obtain more samples for analyzing and writing rules, you can use the following VirusTotal search tags as shown below:
- For example, you can search for a specific serial number and filter by timestamp.
1
2
fs:"2022-03-01T00:00:00+" ( signature:"43 bb 43 7d 60 98 66 28 6d d8 39 e1 d0
03 09 f5" OR signature:"14 78 1b c8 62 e8 dc 50 3a 55 93 46 f5 dc c5 18" )
- For example, you can search for a specific serial number and look for positive detections greater than 5.
1
signature:"0d bf 15 2d ea f0 b9 81 a8 a9 38 d5 3f 76 9d b8" p:5+
There are multiple ways that threat actors can obtain a code signing certificate, such as stealing the certificate from a legitimate organization through system compromise, registering a front company to present to the certificate signing authority as a genuine business, or purchasing a stolen certificate from the underground market.
Writting Detction Rule
We can use YARA’s PE module to write a detection rule that looks for a certificate serial number. The signature object is an array and we can loop through all the certificates in the PE header and look for the one we are interested in. The timestamp is very important to reduce false positives, as this is a valid certificate used to sign legitimate software. We typically determine the known time when the certificate was stolen and search only those files whose compile time is after that. Here is the rule snippet for the rule logic,
1
2
3
4
5
6
7
8
9
10
11
import "pe"
rule cert {
...............
.................
condition:
uint16(0) == 0x5a4d and
pe.timestamp < 1640995200 and
for any i in (0 .. pe.number_of_signatures) :
(pe.signatures[i].serial == "14:78:1b:c8:62:e8:dc:50:3a:55:93:46:f5:dc:c5:18" )
}
Here is one sample YARA rule to detect malware with stolen code signing certificates .
This YARA rule can also be used for threat attribution, as the same certificate may be used to sign other campaigns. However, this attribution is not always accurate, as the same certificate can be shared among different threat actor groups.
I’m linking an article here written by Trend Micro, which I found very insightful in the context of stolen certificates. Have a look, if you have time.