Part 4.3 - Hunting for files with Timestamp Anomalies.
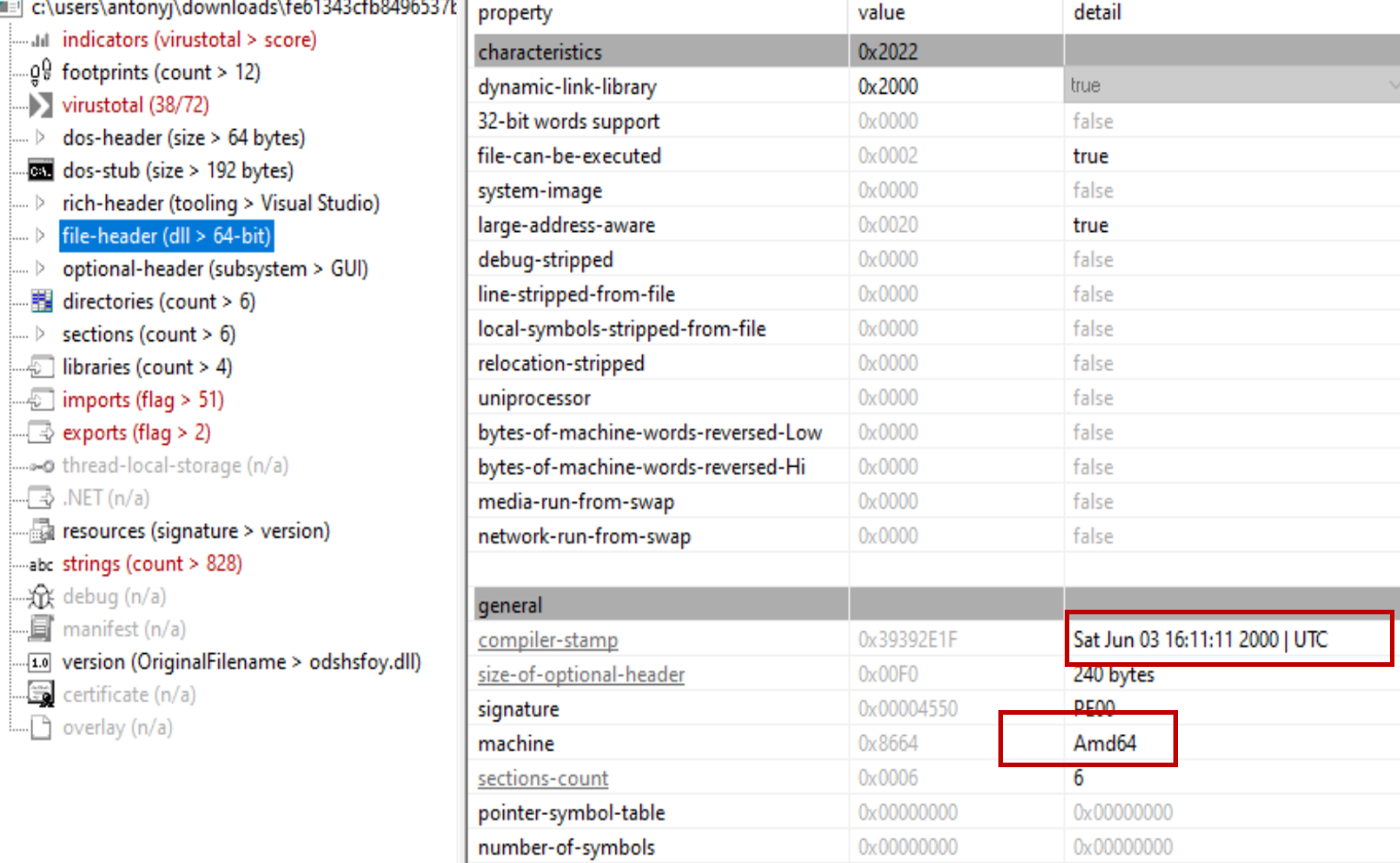
Sometimes, it takes common sense rather than just technical skills to uncover malware code. This example is based on the research published by Kaspersky Labs on TripleFantasy.The research team discovered the following sample, and upon analyzing the basic timestamp details, they noticed that the file was compiled on June 3, 2000, and is a 64-bit binary.
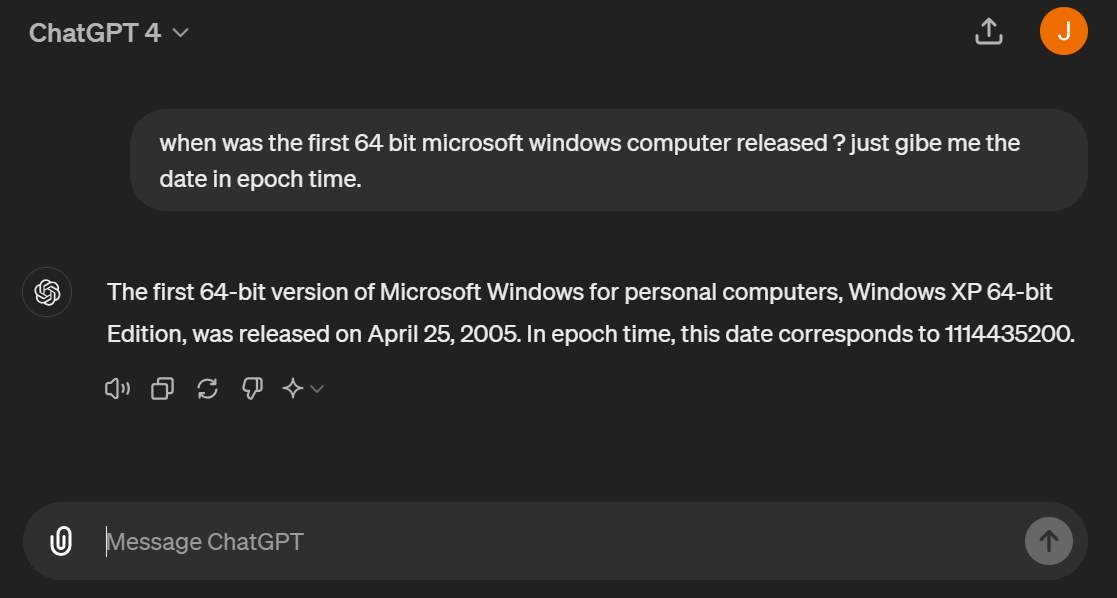
I used ChatGPT to ask a question related to the Windows 64-bit operating system.
This clearly indicates when Microsoft first released the 64-bit operating system. This means the executable should be analyzed.
Here is the YARA rule to look for a Windows 64-bit executable with a specified timestamp:
1
2
3
4
5
6
7
8
import "pe"
rule timestmping
{
condition:
uint16(0) == 0x5A4D and
(pe.machine == pe.MACHINE_AMD64 or pe.machine == pe.MACHINE_IA64) and
pe.timestamp < 1114435200 // April 25 2005
}
This post is licensed under CC BY 4.0 by the author.