What’s Being Proved - Evidence of Execution or Existence?
Revisiting Windows forensics Evidence of Execution artifacts (Windows 10 & later releases)
TL;DR
| Artifact | Execution timestamp | Best Suited for |
|---|---|---|
| Shimcache (artefact : registry) | NO | Evidence of Existence |
| AmCache (artefact : registry) | NO | Evidence of Existence |
| Prefetch (artefact : filesystem) | Yes | Evidence of Execution |
| UserAssist (artefact : registry) | Yes | Evidence of Execution |
| MUICache (artefact : registry) | NO | Evidence of Execution |
| PCA (artefact : filesystem) | Yes | Evidence of Execution |
| SRUM (artefact : filesystem) | NO | Evidence of Execution |
| .Link Files / Jump Lists (artefact : filesystem) | NO | Evidence of Existence |
| ShellBags (artefact : registry) | NO | Evidence of Existence |
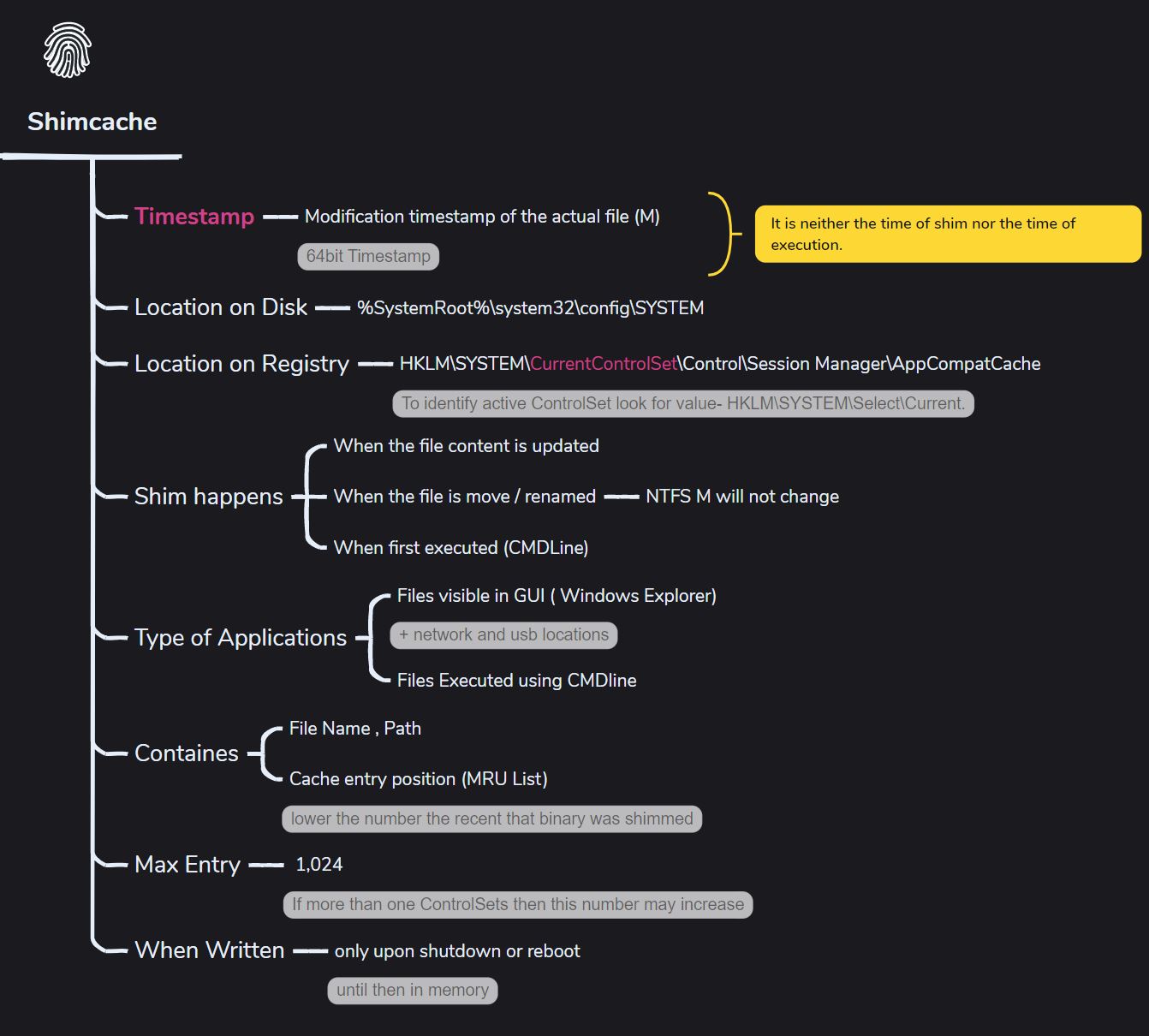
Shimcache /AppCompatCache
What it can prove,
- It indicates if an executable was present on the disk at some time. In some cases, the tools can can flag (for non-Windows native app) executions by analyzing values at the end of files, though this shouldn’t be completely trusted 😔,
- May help to prove that the threat actor accessed OR viewed OR executed files at some point (The most recent entry will be at the top of the list),
- Delected Files : File details remain available even after the threat actor deletes files and prefetch .pf entries from the disk,
- File Renamed : If two or more files in the shim database have the same timestamp but different filenames or paths, it suggests the file was renamed or moved. This is typical when the threat actor drops files and later renames or moves them,. check the ‘cache entry point’ position
- Timestomping : Changing the M/B timestamp won’t affect the shim; the original M timestamp remains preserved. Use M time on shimcache and disk to detect timestamp tampering.
- Use
UsnJrnlto determine the exact time a file was renamed, as ShimCache record only the NTFS M timestamp,
To flush the ShimCache entry from memory to disk, reboot the system after collecting memory data. alternativly use the volatility plugin
windows.shimcachememto collect the ShimCache from memory.
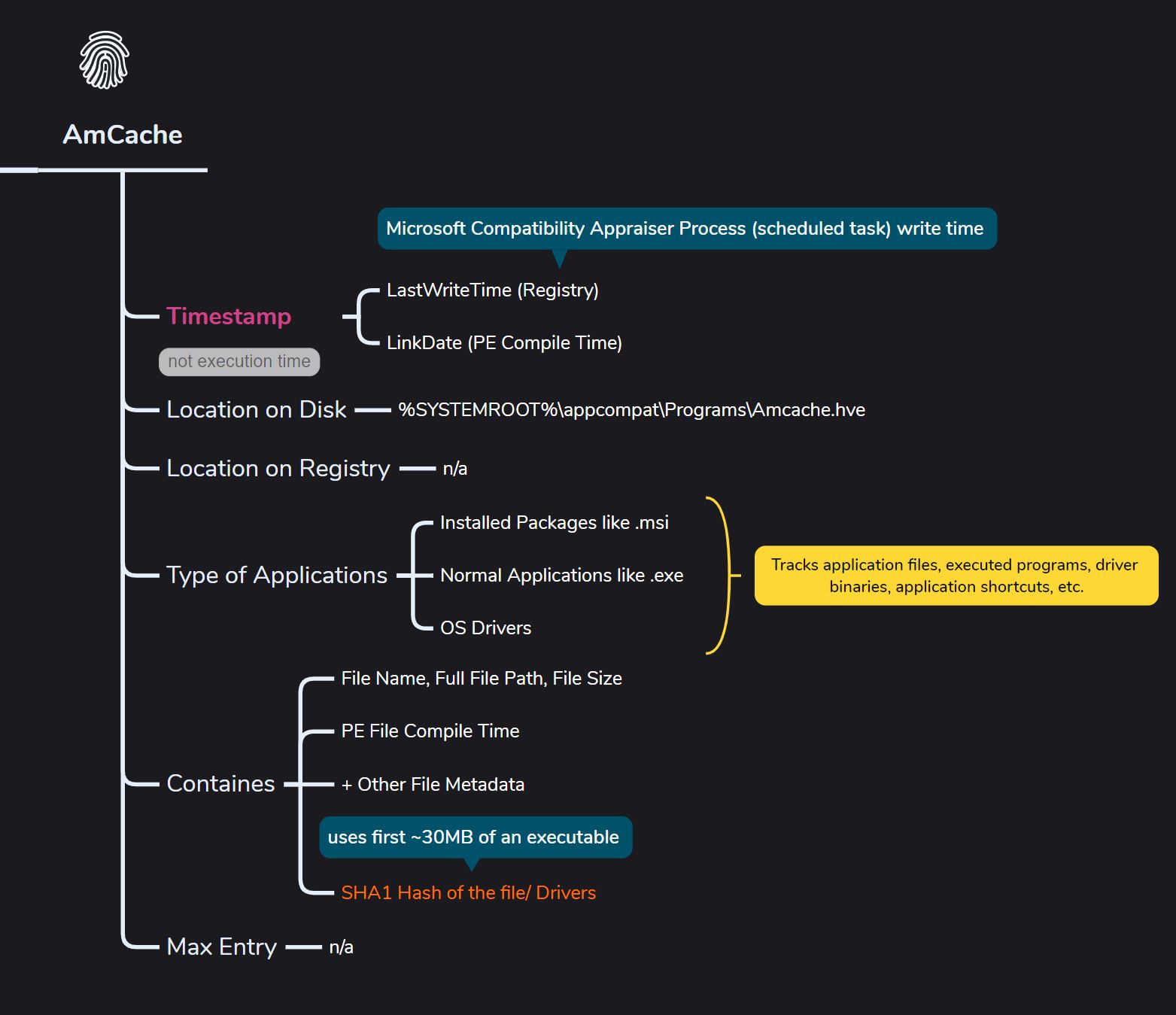
AmCache
What it can prove,
- Entries might come from automated file discovery by the MS Compatibility Appraiser scheduled task (like in Program Files, Program Files (x86), or Desktop) or from program installations—not necessarily from actual file execution.
- Helps track installed applications, executed programs, loaded drivers, and more—making it possible to prove those files existed on the system at some point.
- The last write time in the registry reflects when the scheduled task scanned and updated the entries—not when the program was actually executed.
- The PE header compilation time can help uncover threat intelligence,
- File details can still be recovered even if the threat actor deletes the files and removes the prefetch (.pf) entries from the disk.
- We can cross-reference the PCA ID with the Amcache program ID to confirm that the executable listed in the Amcache hive was actually executed.
Entries may be due to automated file discovery Microsoft Compatibility Appraiser Process (scheduled task)
Notes,
- InventoryApplicationFile = tracks normal excutable
- InventoryApplication = tracks installed application
- InventoryDriverBinary = tracks the loaded drivers
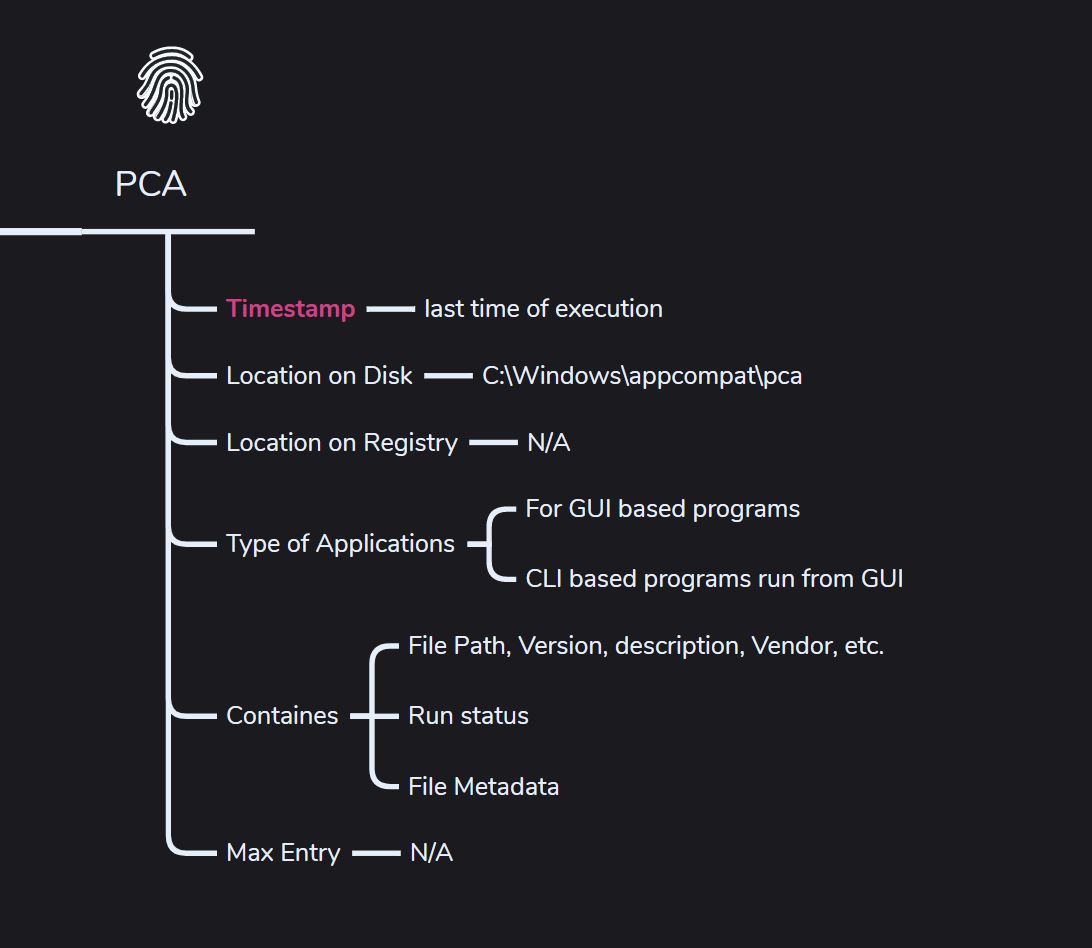
PCA (Win11+)
PCA stands for Program Compatibility Assistant. These artifacts are available as long as the pcasvc service is running on the Windows system.
What it can prove,
- Can identify the last time the program was executed.
- Applications run from the GUI—even those accessed remotely via RDP—are recorded.
- Applications run from the command line, scheduled tasks, or remotely via PsExec aren’t recorded.
- Built-in applications are only recorded if they’re run from a non-default (non-original) directory.
- Can cross-reference the PCA ID with the Amcache program ID to confirm that the executable listed in the Amcache hive was actually run.
- File details can still be available even after the threat actor deletes the files and removes prefetch (.pf) entries from the disk.
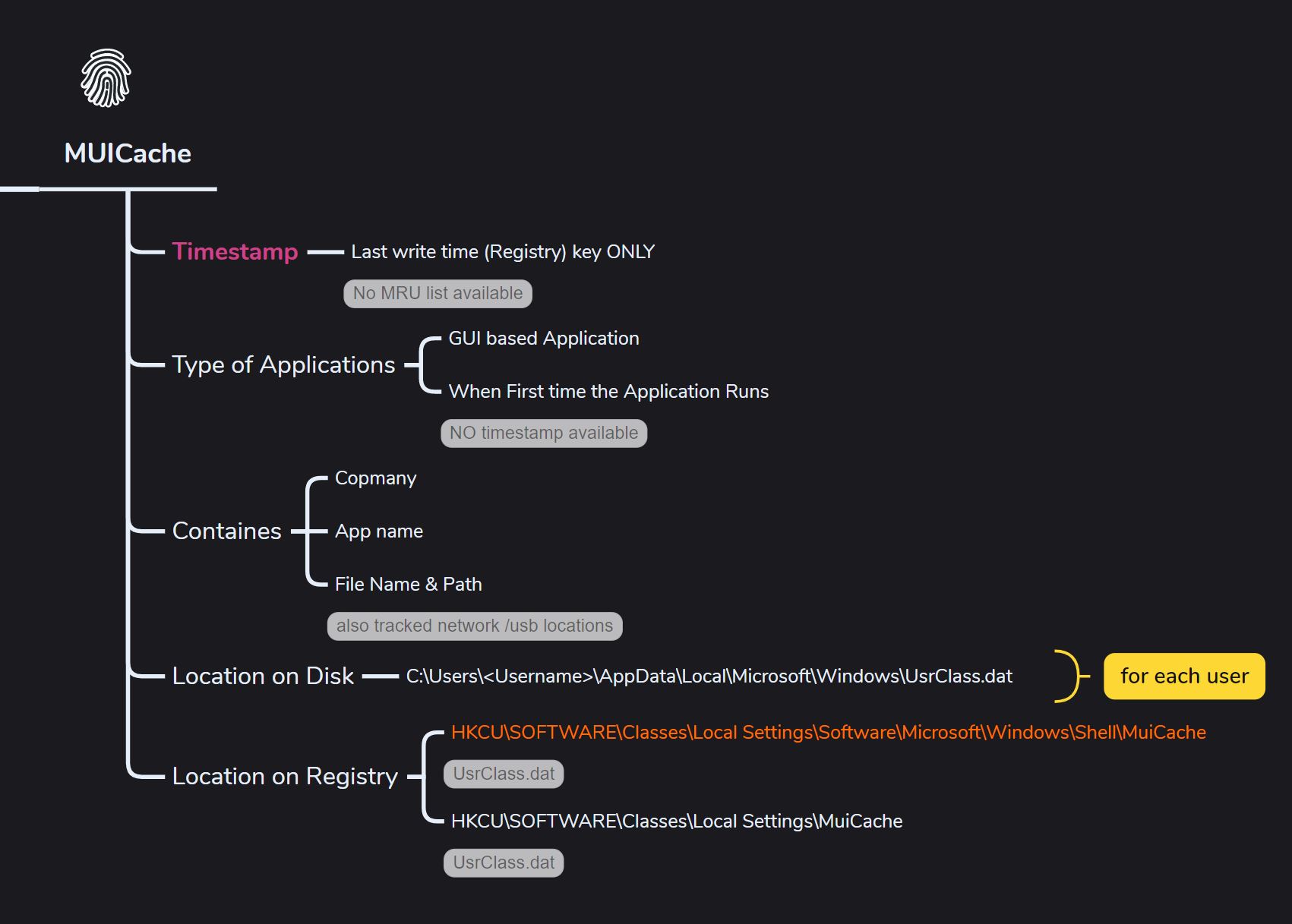
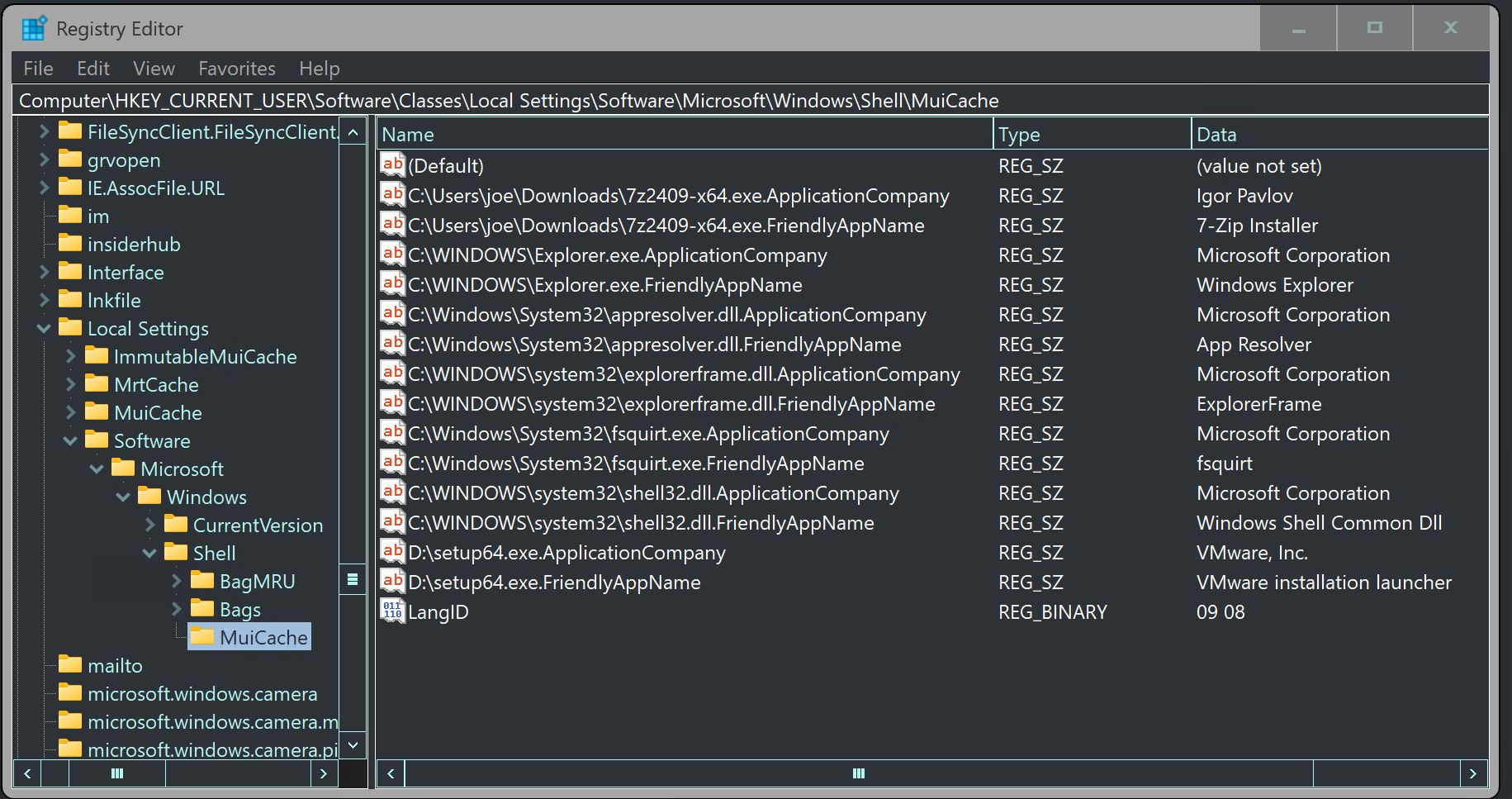
MUICache
Multilingual User Interface service in Windows for lanauge localaiuzation support
What it can prove,
- Helps identify if it’s the first time a GUI-based application has run on the system—even if it came from another device or a network share.
- Helps determine if the threat actor renamed the same files by checking the ApplicationCompany and FriendlyAppName—duplicates often suggest renaming.
- The MUICache includes the LastWriteTime for the registry key, but it doesn’t have an MRU list, making it hard to tell what was written last or in what order.
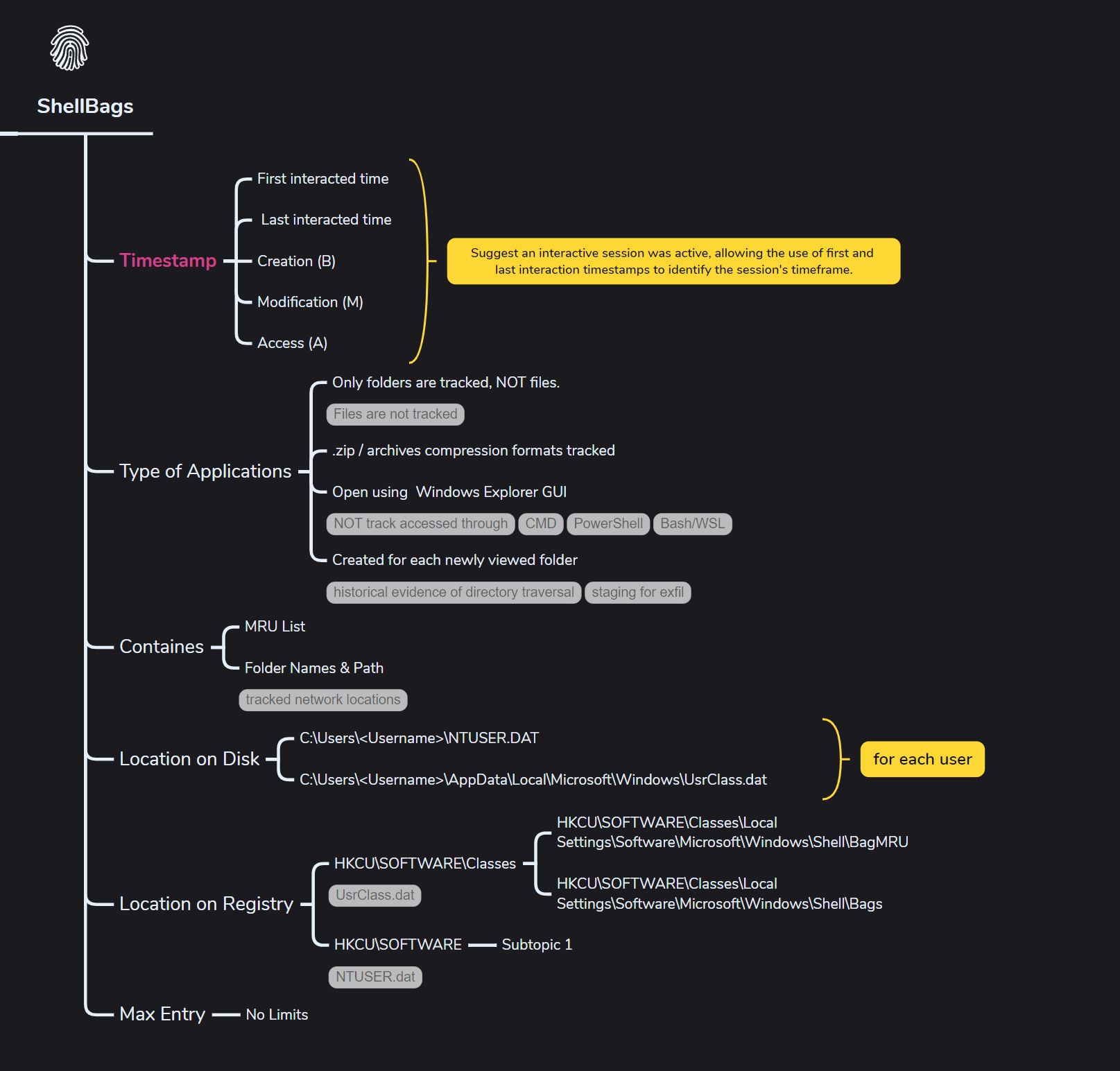
ShellBags
What it can prove,
- can indicate that an interactive session was used.
- First and last interaction timestamps can help pinpoint when the session was active.
- Helps prove the Threat Actor (TA) was browsing through different locations to collect or stage data for later exfiltration.
- Can help prove if someone (like an insider) explicitly viewed a location, even if they later denied it.
Only tracks the folders (and zip archives) viewed via Windows Explorer GUI, not via command line, WSL, PowerShell, etc. Does not track files, only folders.
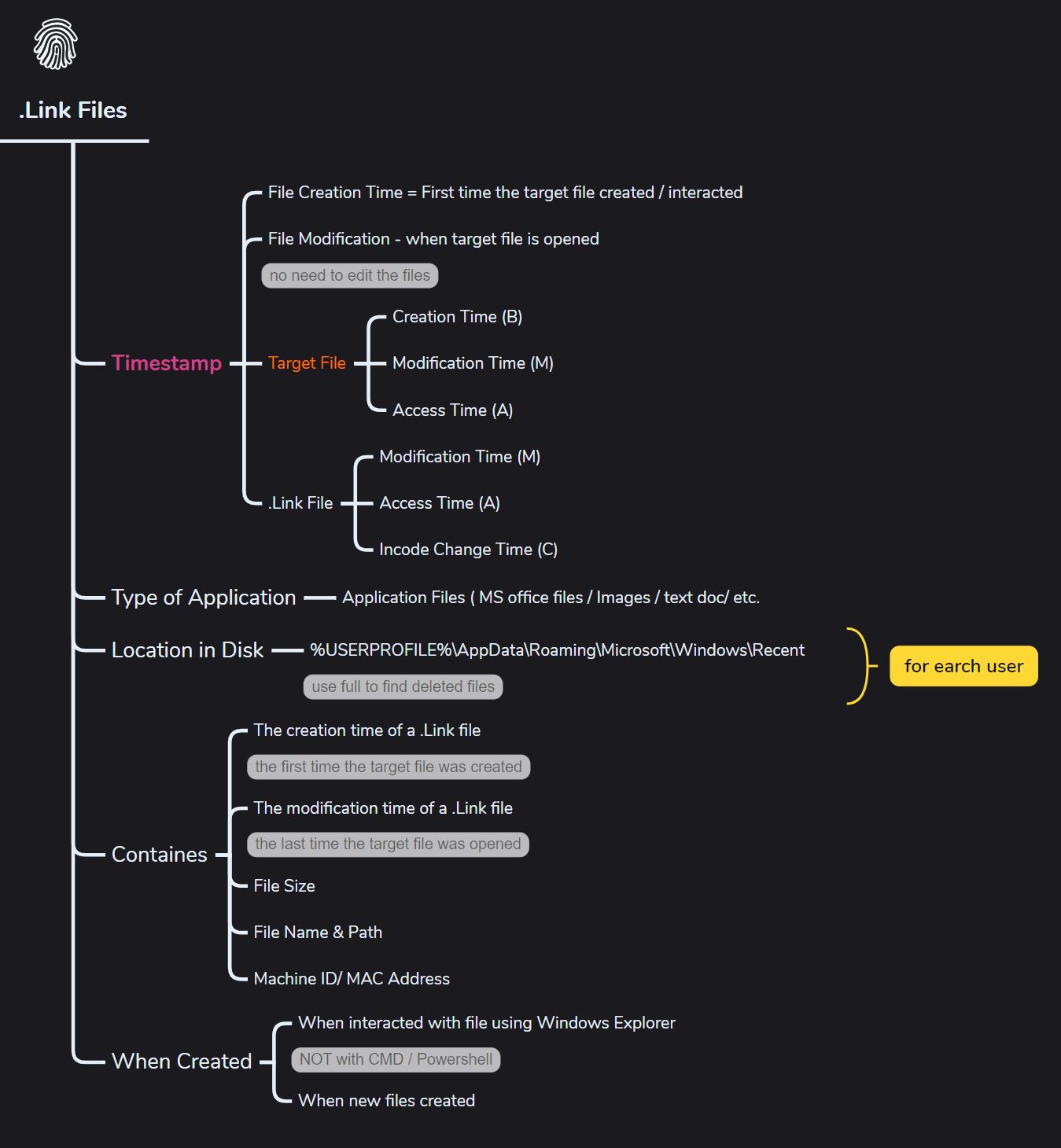
Link Files
What it can prove,
- Shows the threat actor’s interactive use of the system.
- The threat actor accessed the files through the Windows Explorer UI at some point.
- File details can still be available even after the threat actor deletes them from the disk.
- Won’t show files accessed via Command Line or PowerShell.
- Shows the actual size of the file and the machine ID.
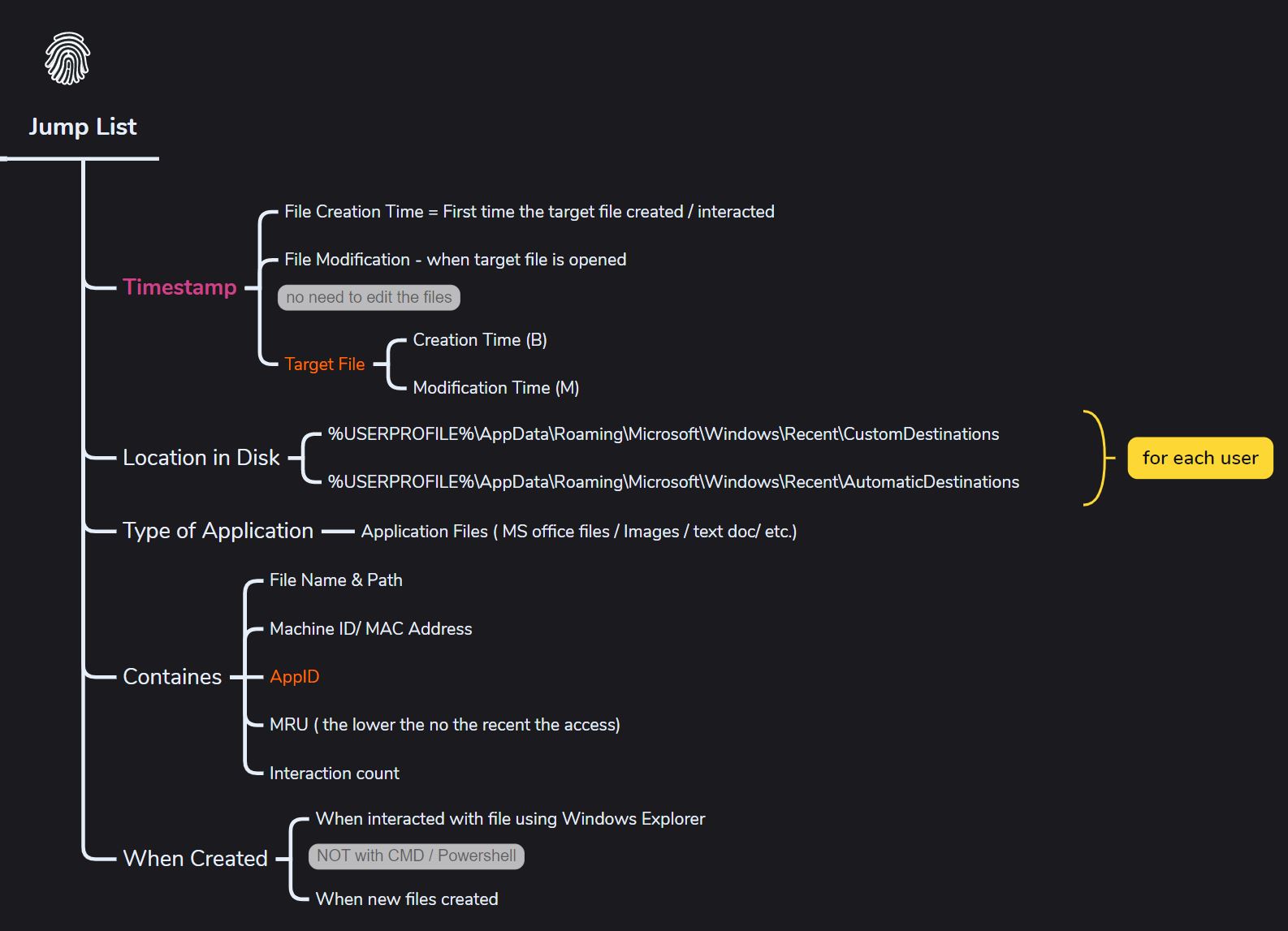
Jump Lists
What it can prove,
- Shows the threat actor’s interactive use of the system.
- The threat actor accessed the files through the Windows Explorer UI at some point.
- File details can still be available even after the threat actor deletes them from the disk.
- Won’t show files accessed via Command Line or PowerShell.
- Shows the actual size of the file and the machine ID.
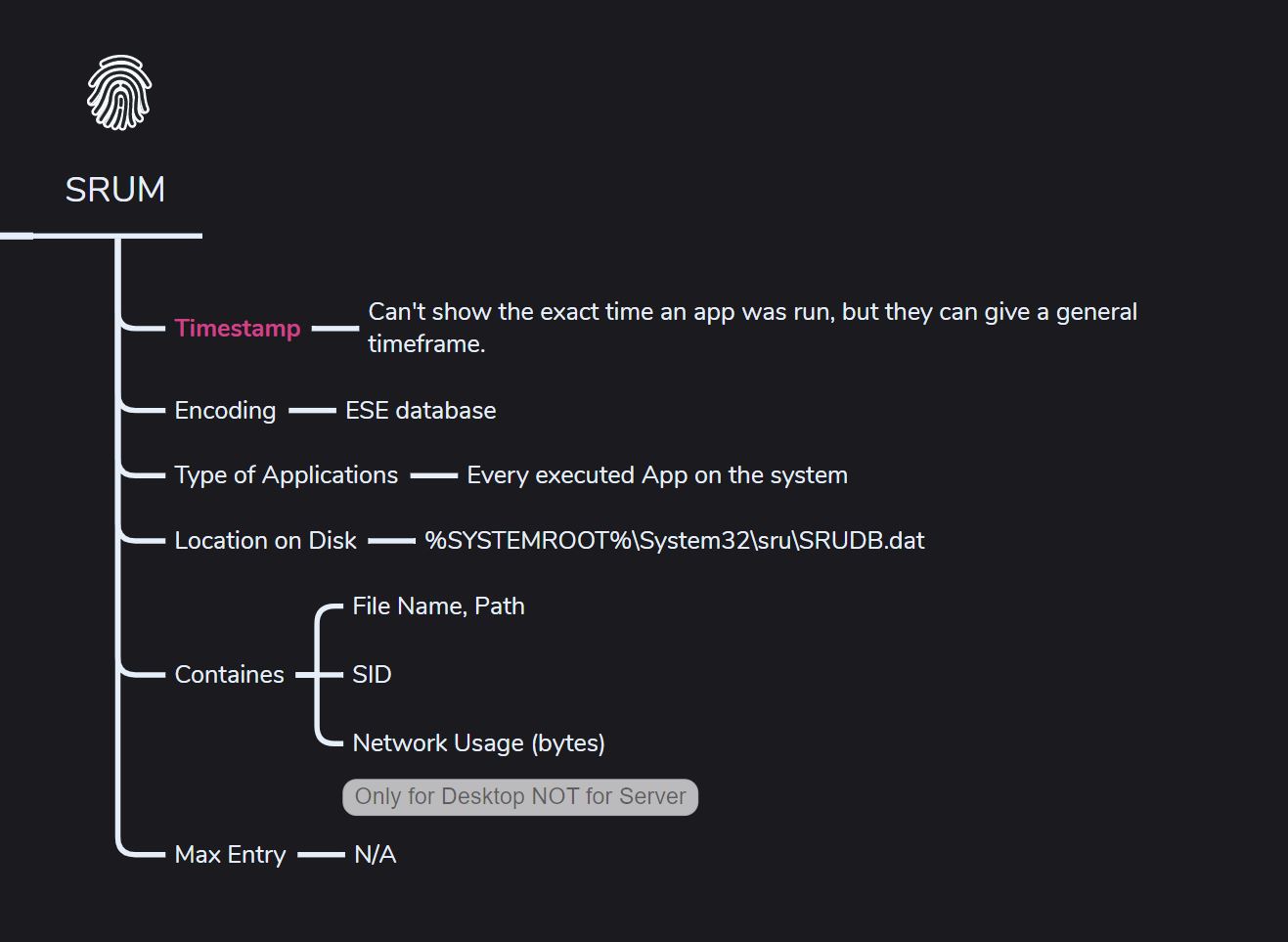
SRUM
What it can prove,
- The timestamp doesn’t show when the app was run—it just marks when the info was added to the SRUM database.
- Shows the executable name, user info, and data in/out, which can help prove data exfiltration.
- Gives insight into how long the application was active on the system.
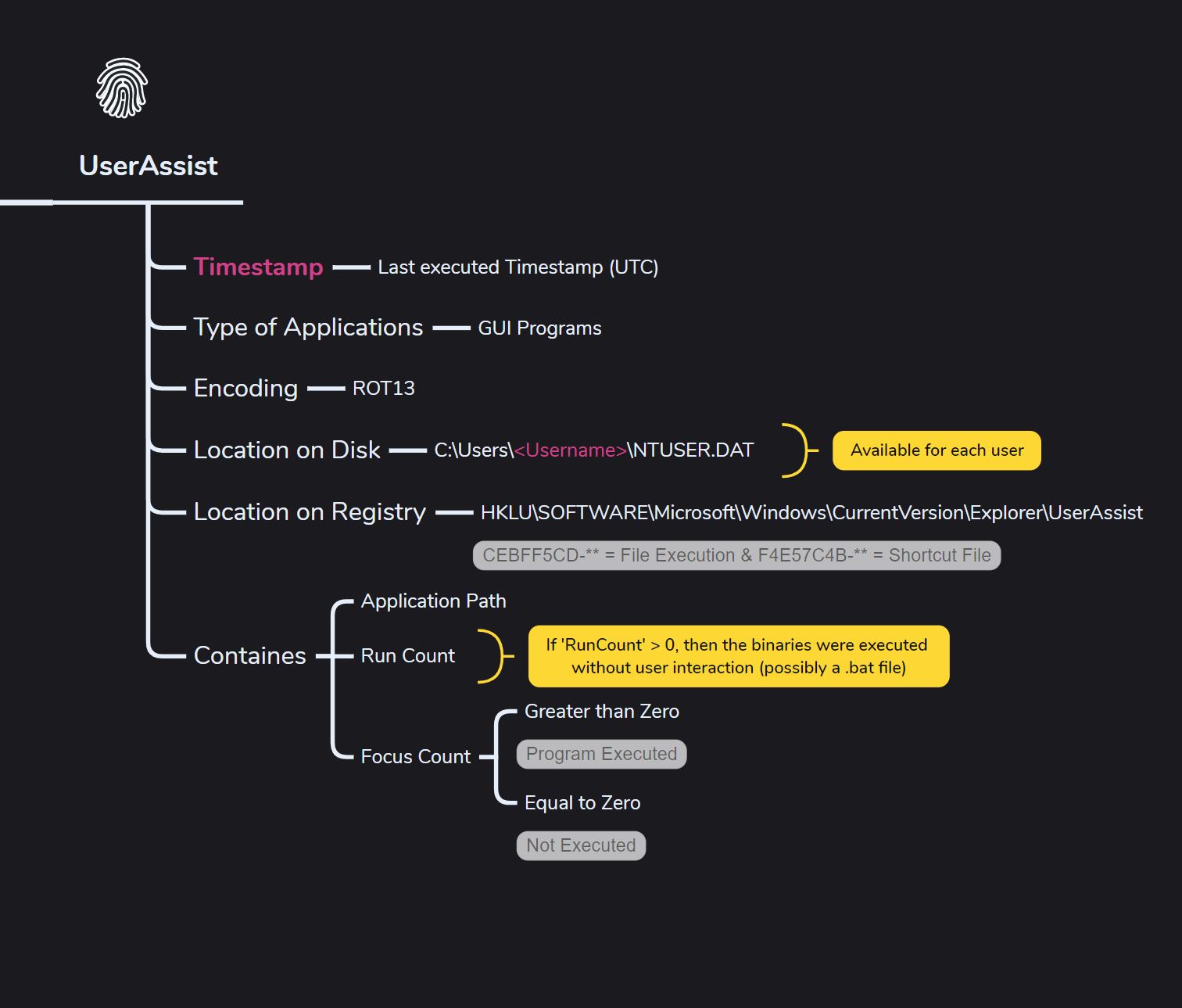
UserAssist
What it can prove,
- It can show that a binary was run if the Focus Time is more than zero.
- When binaries run without user interaction, it’s more important to examine Focus Time than Run Count.
- Just opening a file location can update the UserAssist entries for an executable—this can increase the Run Count and update the Last Executed timestamp, even if the Focus Time doesn’t change.
- Helps determine whether an application was launched from a shortcut (LNK file) or directly from the executable <!–
- If Focus Time = 0, Focus Count > 0 and Last Executed time is not NULL = .bat file no UI
- Runcoutn =0 but last excited not null. Why ? -Understand how entries are created in UserAssist for binaries of interest depending on how they are executed. For example, UserAssist entries will not be created for certain binaries if execution was done through a web browser’s downloads dialog. https://www.magnetforensics.com/blog/artifact-profile-userassist/ –>
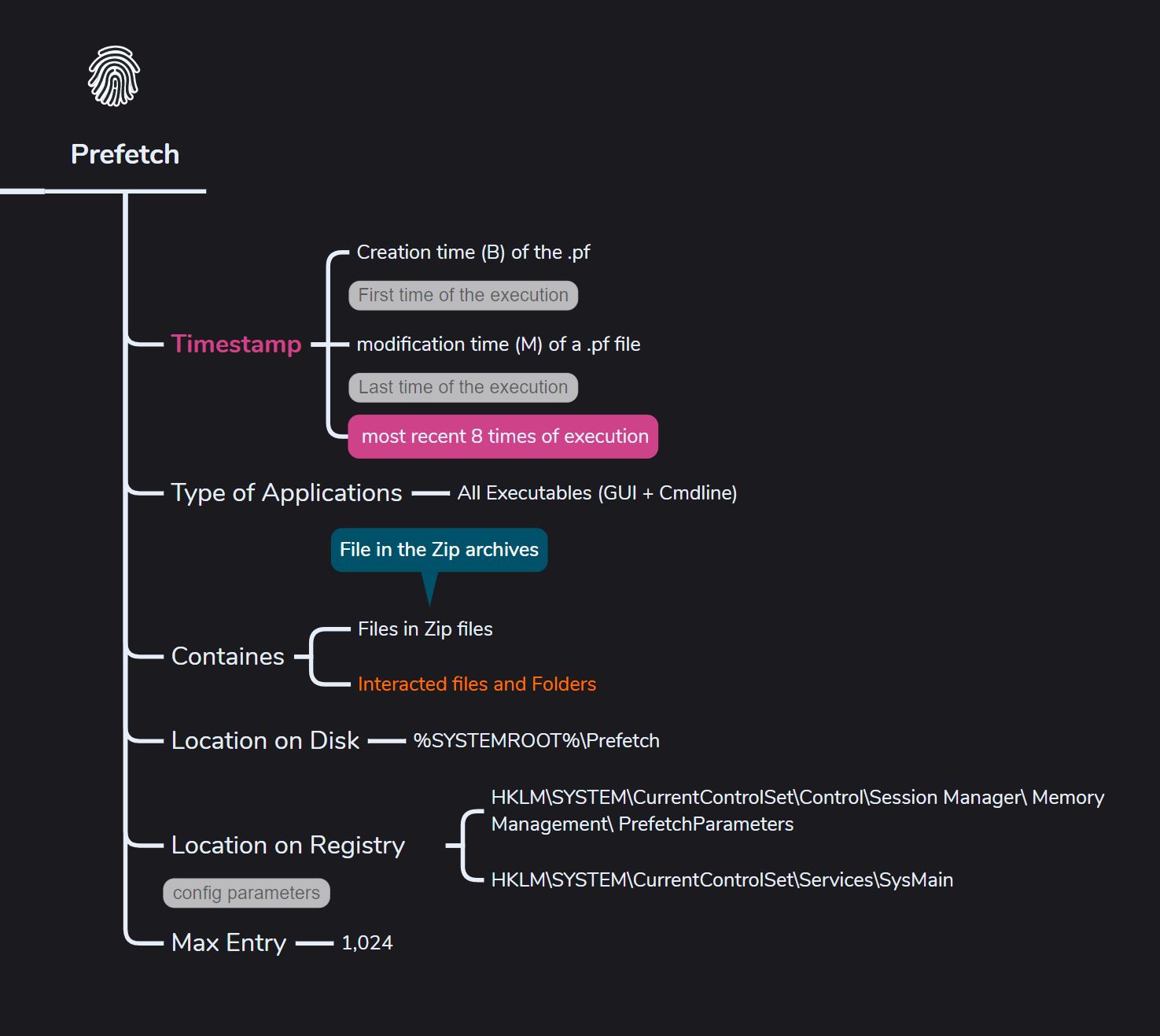
Prefetch
what it can prove,
- Can show that the application was run on the system by a threat actor, but it can’t tell whether the execution was successful or not.
- Helps identify the application’s dependencies, like DLLs and other components it interacted with to run.
- It can also help identify the files contained within a zip archive
- Can still show that files were executed by the threat actor, even if they were later removed or deleted from the disk.
- Can cross-reference .pf files with MFT entries on the NTFS file system to get a clearer picture of file execution and activity.
- Can cross-reference the execution with UserAssist entries if it was a GUI-based application.
Sometimes, you’ll find multiple entries in the folder for the same executabl
| Exec | senarios |
|---|---|
| SVCHOST.exe | Always runs with parameters, so you’ll usually see more than one .pf file created for it. |
| RUN32DLL.exe | Always runs with parameters, so you’ll usually see more than one .pf file created for it. |
| CMD.exe | You might see more than one entry because of different execution paths—like 32-bit /64-bit. |